Recently I’ve tested the FortiOS 7.0 and I was wondering about the SAML connection towards Azure for login via Microsoft and the use of Multifactor Authentication. I have noticed there are some improvements. How ever, some features or functions are missing in the GUI.
In general you need to configure the SAML though the CLI. You can use the GUI-CLI or connect with SSH to your firewall. It’s up for your own preference. In my example I used the GUI-CLI version to make some references. In basic the following instructions in the fortigate cookbook: Configuring SAML SSO login for SSL VPN web mode with Azure AD acting as SAML IdP are clear.
You need to take some extra noted when you want to use a group. the setup should look like this.
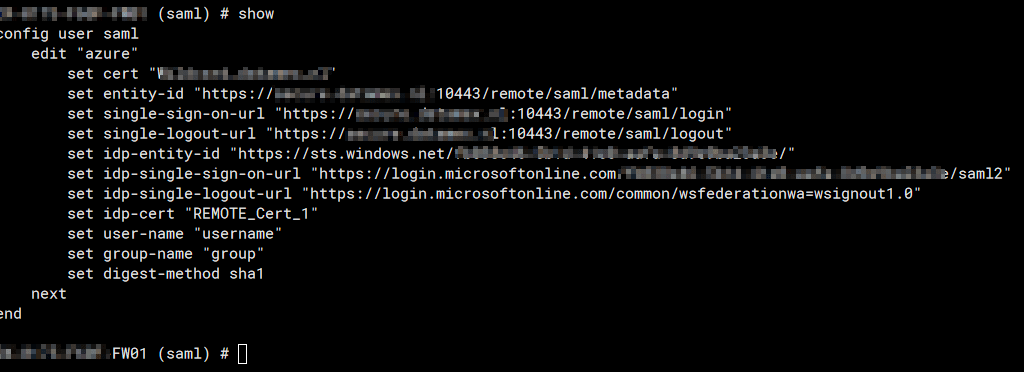
The interesting part what you can’t configure yet properly in the GUI is the Group Access setup

In the config user group you create the group you want to use for the SAML setup. You relate the earlier SAML user setup to this group. It’s pretty straight forward in this case. But when you go back to the gui when you finished the configuration. you will notices under users & groups

That the members are filled in. If you are running 6.4 than you won’t see the member in this list. Now you can edit this group also.

You will see a remote server. Which is common if you use LDAP or Radius. When you edit this remote server this server you will notice that the Fortigate will inform you that this group is a SAML SSO Server when you click on the Azure name

This part is not yet available in the GUI. I hope Fortinet will add this to the GUI to make it more user friendly. I’m not scared to use the CLI, but other people might love to use the GUI above the CLI.
When you try to add a new remote server.

You won’t be able to select the SAML SSO Server
It’s not a bug I think just a missing Gui option which should be there if you give the LDAP and Radius server options as possibilities to use.