After struggling with a routing problem between a host which had a Cisco ASA with an ASA version 8.4(3) as gateway and had to route to an other subnet in the inside area.
In this example the host 172.16.1.1 wants to connect to a http://10.1.10.1 (icmp works, other traffic doesn’t)
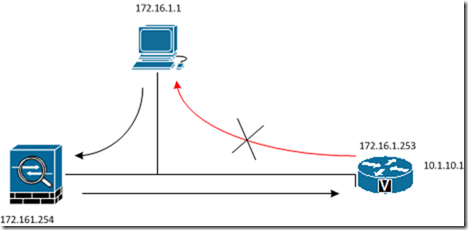
To solve this issue, you need to add some configuration to the Cisco ASA ( 172.16.1.254 ) as a workaround. The Cisco ASA is not really designed to do routing, if i’m correct.
However what should you add to the configuration.
You need a static route added to the Cisco ASA for example:
route inside 10.1.10.0 255.255.255.248 172.16.1.253 1
Access-list you have to create:
access-list tcp_state_bypass extended permit tcp any any
Create a class map and a policy map:
class-map tcp_bypass match access-list tcp_state_bypass ! ! policy-map tcp_bypass_policy class tcp_bypass set connection advanced-options tcp-state-bypass
Configure a service-policy to make it active.
service-policy tcp_bypass_policy global

Thanks for that, this was really useful for me !
Please let me add some info to be more secure (tested on my network) :
– your access-list should be more restrictive and only content the wanted address/network
for example, here : access-list tcp_state_bypass extended permit tcp 172.16.1.0 255.255.255.0 10.1.10.0 255.255.255.0
– applying that on global Policy is “to much” you can only apply that on Inside interface :
service-policy tcp_bypass_policy interface Inside
Hope this helps !
Thank for your input. It’s interesting to know.
This small change is better. I had issues configuring an ASA 5506 with Firepower doing the re-route from the ASA to the Firepower module. With the access list set to any any, it was incorrectly permitting traffic that was supposed to be rerouted to the firepower module.